Incident Response Plan
Purpose
This document describes the plan for responding to information security incidents at Keuka College. It defines the roles and responsibilities of participants, characterization of incidents, and reporting requirements. The goal of the Incident Response Plan is to prepare for, detect and react to computer security incidents, determine their scope and risk, respond appropriately to that incident, communicate the results and risk to all stakeholders, and reduce the likelihood of the incident from reoccurring.
Scope
This plan applies to the information systems, institutional data, and networks of Keuka College and any person or device who gains access to these systems or data.
Maintenance
The College’s Information Technology Department is responsible for the maintenance and revision of this document. The Associate Vice President in coordination with the Information Security and Systems Administrators are charged will executing this plan.
Relationship to Other Groups at Keuka College
The Information Technology Department acts on behalf of the College community and will ask for cooperation and assistance from community members as required. The Information Technology Department also works closely with the College's administration and counsel in investigations, and at their behest may assist law enforcement.
Definitions
Events
An event is any observable occurrence in a system or network. This policy will address only adverse events. Adverse events are events with a negative consequence such as system crashes, packet floods, unauthorized use of system, unauthorized access to sensitive data, and execution of malware that destroys data. Not all events become incidents
Incident
A computer incident as defined by the National Institute of Standards and Technology (NIST) Special Publication 800-61 Revision 2 is a violation or imminent threat of violation of computer security policies, acceptable use policies, or standard computer security practices. A Keuka College computer security incident could also include a violation to other school policies, standard, or code of conduct; or threatens the confidentiality, integrity, or availability of information systems or institutional data.
Incidents may be established by review of a variety of sources including, but not limited to Information Technology Department monitoring systems, reports from Keuka College staff or outside organizations and service degradations or outages. Discovered incidents will be declared and documented by the Information Technology Department.
Complete IT service outages may also be caused by security-‐related incidents, but service outage procedures will be detailed in disaster recovery procedures.
Incidents will be categorized according to the potential negative impact on the confidentiality, integrity, and/or availability of Keuka College information technology resource or criticality of resource using a Low-Medium-High designation. The initial severity rating may be adjusted during plan execution.
Detected vulnerabilities will not be classified as incidents. The Information Technology Department employs tools to scan the environment, and depending on severity of found vulnerabilities may warn affected users, disconnect affected machines, or apply other mitigations. In the absence of indications of sensitive data exposure, vulnerabilities will be communicated, and the Information Technology Department will deploy remediation within reason to reduce that risk.
Incidents can include:
• Malware/viruses/Trojans.
• Ransomware.
• Phishing.
• Unauthorized electronic access
• Breach of information, including PII and PHI
• Unusual, unexplained or repeated loss of connectivity.
• Unauthorized physical access.
• Loss or destruction of physical files, etc.
Personally Identifiable Information (PII)
For the purpose of meeting security breach notification requirements, PII is defined as a person’s first name or first initial and last name in combination with one or more of the following data elements:
- Social security number
- State-issued driver’s license number
- State-issued identification card number
- Student ID Card
- Financial account number in combination with a security code, access code or password that would permit access to the account
- Medical and/or health insurance information
Protected Health Information (PHI)
PHI is defined as "individually identifiable health information" transmitted by electronic media, maintained in electronic media or transmitted or maintained in any other form or medium by a covered entity, as defined by HIPAA. PHI is considered individually identifiable if it contains one or more of the following identifiers:
• Name
• Address
• All elements of dates (except year) related to an individual including birth date, admissions date, discharge date, date of death and exact age if over 89)
• Telephone numbers
• Fax numbers
• Electronic mail addresses
• Social security numbers
• Medical record numbers
• Health plan beneficiary numbers
• Account numbers
• Certificate/license numbers
• Vehicle identifiers and serial numbers, including license plate number
• Device identifiers and serial numbers
• Internet protocol (IP) addresses
• Biometric identifiers, including finger and voice prints
• Full face photographic images and any comparable images
• Any other unique identifying number, characteristic or code that could identify an individual
PHI does not include education records or treatment records covered by the Family Educational Rights and Privacy Act or employment records held by the school in its role as an employer.
Incident Response
An action plan for handling the misuse of information system resources.
Compromised Computer
Any computer source whose confidentiality, integrity or availability has been adversely impacted, either intentionally or unintentionally, by an untrusted source. A compromise can occur either through manual interaction by the untrusted source or through automation.
Evidence Preservation
The goal of any incident response is to reduce and contain the impact of an incident and ensure that information security related assets are returned to service in the timeliest manner possible. The need for a rapid response is balanced by the need to collect and preserve evidence in a manner consistent with state and federal laws, and to abide by legal and administrative requirements for documentation and chain-of-custody.
Roles and Responsibilities
Incident Response Team
The Incident Response Team is led by the Associate Vice President of Technical Solutions, or a designee named by them, or other executive leadership. The mission of Incident Response Team is to provide an immediate, effective, and skillful response to any unexpected incident with information security implications (i.e., negatively impacting the confidentiality, integrity, or availability of Keuka College systems or data). The Incident Response Team is expected to follow the Incident Response Plan and is authorized to take appropriate steps to contain and remediate an incident.
Incident Response Coordinator
The Incident Response Coordinators are the Associate Director of Information Technology and the Systems Administrator and are responsible for assembling all the data pertinent to an incident, communicating with appropriate parties, ensuring that the information is complete, and reporting on incident status both during and after the investigation.
Incident Response Handlers
Incident Response Handlers are Keuka College Information Technology Department staff, or outside contracted services who gather, preserve, and analyze evidence so that an incident can be brought to a conclusion.
Communication Lead
The Vice President overseeing Communications leads the effort on messaging and communication for all audiences, inside and outside of the company.
Law Enforcement
Law Enforcement includes federal and state law enforcement agencies, and U.S. government agencies that present warrants or subpoenas for the disclosure of information. Interactions with these groups will be coordinated with the Vice President overseeing communications at Keuka College and counsel.
Counsel
The Keuka College’s general counsel is the liaison between the Vice President overseeing Communications and outside Law Enforcement and will provide counsel on the extent and form of all disclosures to law enforcement and the public.
Users
Users are members of the Keuka College community or anyone accessing an information system, institutional data or Keuka College network who may be affected by an incident.
Methodology
This plan outlines the most general tasks for incident response and will be supplemented by specific internal guidelines and procedures that describe the use of security tools and/or channels of communication. The Disaster Recovery Plan is supplemental to the Incident Response Plan. Not all events will rise to the level of "Disaster Recovery." These internal guidelines and procedures are subject to amendment as technology changes. It is assumed that these guidelines will be documented in detail and kept up to date.
Evidence Preservation
The goal of incident response is to reduce and contain the scope of an incident and ensure that IT assets are returned to service as quickly as possible. Rapid response is balanced by the requirement to collect and preserve evidence to abide by legal and administrative requirements for documentation and chain of custody. The Information Technology Department will maintain and disseminate procedures to clarify specific activities in the Information Technology Department and in Keuka College departments with regard to evidence preservation and will adjust those procedures as technologies change.
Capability, Resiliency
The Information Technology Department will endeavor to maintain sufficient staffing and third-party augmentation to investigate each incident to completion and communicate its status to other parties while it monitors the tools that detect new events. Insufficient staffing will impact rapid response capability and resiliency, as will degradation of the tools used for detection, monitoring, and response.
Incident Response Phases
The basic incident process encompasses four phases: preparation, detection and analysis, containment eradication and recovery and post-incident activity. The dynamic relationship between those phases is highlighted in Figure 1. These phases are defined in NIST SP 800-61 (Computer Security Incident Handling Guide). This plan is the primary guide to the preparation phase; local guidelines and procedures will allow the Information Technology Department to be ready to respond to any incident. Recovery includes re-evaluating whether the preparation or specific procedures used in each phase are appropriate and modifying them if inappropriate.
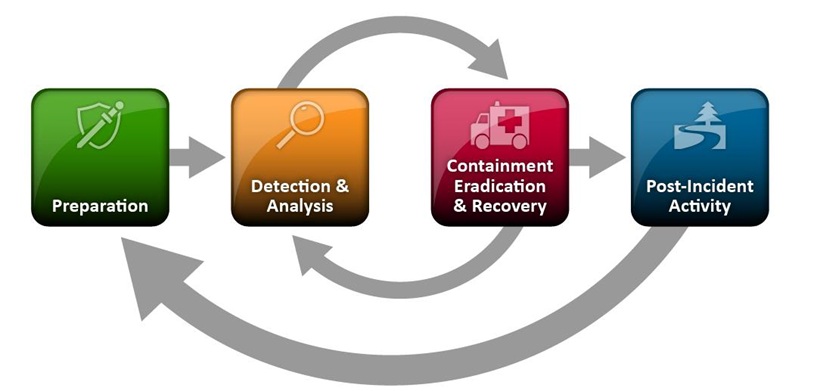
Figure 1: Incident Response Phases – NIST SP 800-61 rev2
Preparation
Preparation includes those activities that enable the Information Technology Department to respond to an incident: policies, tools, procedures, effective governance, and communication plans. Preparation also implies that the affected groups have instituted the controls necessary to recover and continue operations after an incident is discovered. Post-mortem analyses from prior incidents should form the basis for continuous improvement of this stage. Keuka College utilizes several mechanisms to prevent, and prepare to respond to, an incident.
Security Awareness Training: All personnel are required to take security awareness training annually. This training covers additional ongoing threats to systems such as malware, phishing, social engineering, ransomware, and other threats as they become known.
Malware/Antivirus/Spyware Protections: All information system terminals, as well as key information flow points on the network are protected by continuous defense against malware/antivirus/spyware and other known malicious attacks. These defense mechanisms are kept up to date without the need for end user intervention, and end users are restricted from accessing, modifying, disabling, or making other changes to the defense mechanisms.
Firewall and Intrusion Prevention Devices (IPD): Firewall and IPD are in place to provide the necessary depth of defense. The Information Technology Department keeps all firewalls and IPD up to date with the latest security patches and other relevant upgrades, as well as maintain an active backup of the latest security configuration.
Physical Security Measures: Training and policies for employees to ensure they are keeping their workspace attended and secure.
Event Logs: Event logging is maintained at all applicable levels, capturing events and is retained for the specified period, and reviewed regularly.
Patching/Updating: Systems shall be patched and updated as new security patches and hot fixes are released. Any software or hardware product that reaches the end of the manufacturers service and support life for patching will be deemed out-of-compliance and replace within commercially reasonable efforts.
Detection & Analysis
Detection is the discovery of the event with security tools or notification by an inside or outside party about a suspected incident. The detection of an incident requires the immediate activation of the Incident Response Team. The determination of a security incident can arise from one or several circumstances simultaneously. Means by which detection can occur include:
- Trained personnel reviewing collected event data for evidence of compromise.
- Software applications analyzing events, trends, and patterns of behavior.
- Intrusion Protection/Intrusion Detection devices alerting to unusual network or port traffic.
- The observation of suspicious or anomalous activity within a Keuka College facility or on a computer system.
It is critical in this phase:
- To detect whether a security incident has occurred.
- To determine the method of attack.
- To determine the impact of the incident to the mission, systems, and personnel involved in the incident.
- To obtain or create intelligence products regarding attack modes and methods.
Analysis of the incident indicators will be performed in a manner consistent with the type of incident. In the event of a physical incident, appropriate steps will be taken to determine weaknesses in either the physical security of the facility, its monitoring tools, or its training programs to assess areas for process improvement or change. For an electronic incident, Keuka College’s Systems Administrator, aided by a managed service provider and cybersecurity consultants when needed, will perform static and dynamic analysis of malicious code, a review of information system boundary protections, determination of source code if applicable, the depth and breadth of the attack, if the attack has migrated to other systems on or off the network, and any other tasks appropriate to the type of incident experienced. These analyses can be performed either manually or utilizing automated tools dependent upon the situation, timeliness, and availability of resources.
Incident Categories
An incident will be categorized as one of three severity levels, Low-Medium-High. These severity levels are based on the impact on Keuka College and can be expressed in terms of financial impact, impact to services and/or performance of our mission functions, or impact to Keuka College’s image. See the Disaster Recovery Plan for further information incident classification.
Containment
Containment is the triage phase where the affected host or system is identified, isolated, or otherwise mitigated, and when affected parties are notified and investigative status established. Containment activities for security incidents involve decision-making and the application of strategies to help control attacks and damage, cease attack activities, or reduce the impact or damage caused by the incident. Information Security and Systems Administrator or contracted security vendor are responsible for containment and will document all containment activities during an incident.
Eradication
The Information Security and Systems Administrator, or contracted security vendor is responsible for eradication and will document all eradication activities during an incident.
Eradication efforts for a security incident involve removal of latent threats from systems (such as malware on the system and user accounts that may have been created), identifying and mitigating potential vulnerabilities or misconfigurations that may have been exploited, and identification of other hosts that may have been affected within the organization.
Recovery
Information Security and Systems Administrator or contracted security vendor is responsible for recovery and will document all recovery activities during an incident. Recovery efforts for incidents will involve the restoration of affected systems to normal operation. This is dependent upon the type of incident experienced but may include actions such as restoring systems from backups, rebuilding systems, replacing compromised files with clean versions, installing patches, changing passwords, and increasing network perimeter and host-based security.
Post-Incident Activity
Information Security and Systems Administrator and the Associate Director of Information Technology are responsible for documenting and communicating post-incident activity. Post-incident activities will occur after the detection incident activities involve the reflection, compilation, and analysis of the activities that occurred leading to the security incident, and the actions taken by those involved in the security incident, including the incident response team. Important items to be reviewed and considered for documentation are:
• Exactly what happened, and at what times?
• How well did staff and management perform in dealing with the incident?
• What information was needed sooner?
• Were any steps or actions taken that might have inhibited the recovery?
• What should be done differently the next time a similar incident occurs?
• How could information sharing with other organizations have been improved?
• What corrective actions can prevent similar actions in the future?
• What precursors or indicators should be watched for in the future to detect similar incidents?
• What additional tools or resources are needed to detect, analyze, and mitigate future incidents?
Post-incident activities will be incorporated into future training opportunities for all parties involved in the incident, from victims, to system administration personnel, to incident responders.
Escalation
The escalation process will be initiated to involve other appropriate resources as the incident increases in scope and impact. Incidents should be handled at the lowest escalation level that can respond to the incident with as few resources as possible in order to reduce the total impact and maintain limits on cyber-incident knowledge.
The Incident Response Team will consider several characteristics of the incident before escalating the response to a higher level. They are:
• How widespread is the incident?
• What is the impact to business operations?
• How difficult is it to contain the incident?
• How fast is the incident propagating?
• What is the estimated financial impact on Keuka College?
• Will this negatively affect Keuka College’s image?
At any time during the incident response process, the Incident Response Coordinators may be called upon to escalate any issue regarding the process or incident.
The Incident Response Team and counsel will determine if and when an incident should be escalated to external authorities.
Guidelines for the Incident Response Process
In the process of responding to an incident, many questions arise and problems are encountered, any of which may be different for each incident. This section provides guidelines for addressing common issues. The Associate Vice President of Technical Solutions should be consulted for questions and incident types not covered by these guidelines.
Insider Threats
In the case that a particular Incident Response Handler is a person of interest in an incident, the Incident Response Coordinator will assign other Incident Response Handlers to the incident.
In the case that the Incident Response Coordinator is a person of interest in an incident, the Associate Vice President of Technical Solutions will act in their stead or appoint a designee to act on their behalf.
In the case that the Associate Vice President of Technical Solutions is a person of interest in an incident, the Vice President overseeing the Information Technology Department will act in their stead or appoint a designee to act on their behalf.
In the case that another Keuka College administrative authority is a person of interest in an incident, the Information Technology Department will work with the remaining administrative authorities in the Information Technology Department’s reporting line to designate a particular point of contact or protocol for communications.
Communications Plan
All public communications about an incident or incident response to external parties outside of Keuka College are made in consultation with counsel and the Vice President overseeing Communications. Private communications with other affected or interested parties contain the minimum information necessary. The minimum information necessary to share for a particular incident is determined by the Vice President overseeing the IT Department.
Privacy
The Acceptable Use Policy provides specific requirements for maintaining the privacy of school affiliates. All incident response procedures will follow the current privacy requirements as set out in the Acceptable Use Policy. Exceptions must be approved by Associate Vice President of Technical Solutions.